Intel SGX Software Stack Demystified
The software stack for developing and launching Intel SGX enclaves is such a mess. Parts of this is due to confusing naming, and lack of centralized documentations. This post the process of me trying make sense of it from a developer point of view.
The software stack
There are awfully lots of moving parts involved in launching an SGX enclave.
- The SGX Driver allows interaction with SGX hardware components. The driver uses privileged instruction for enclave management (e.g.,
ECREATE,EADD,EEXTEND). Three endpoints are exposed to the userspace, which are communicated with through IOCTL APIs.-
/dev/sgx_enclaveprovides APIs for enclave management (2). Some of the APIs:-
SGX_IOC_ENCLAVE_CREATEallocates kernel structures and invokesECREATEto create an enclave. -
SGX_IOC_ENCLAVE_ADD_PAGESadd pages to uninitialized enclaves and also optionally extends its measurement. -
SGX_IOC_ENCLAVE_INITfinalize enclave initialization.
-
-
/dev/sgx_provision: Not sure what it does currently, probably related to secret provisioning. -
/dev/sgx_vepc(the virtual EPC) support launching SGX enclave in guest virtual machines.
-
- Intel PSW (Platform SoftWare) is the userspace component in charge of launching enclaves and provide runtime services (key provisioning, remote attestation).
- Intel SGX SDK Contains libraries and tools that is used to develop SGX applications.
- The library is divided into 3 functional components (1):
- Trusted RunTime System (TRTS) is linked with the user enclave code
- Untrusted RunTime System (URTS) is linked with the untrusted part of the application that set up the enclave application by communicating with the
aesm_servicethrough sockets and pipes. - The Enclave standard library provides minimal standard C/C++ functionalities (except for I/O related tasks)
- THe SDK also provides utility for building and distributing enclaves:
-
Edger8rconverts EDL files into actual interface implementation. -
sgx_signsigns enclave binaries -
sgx-gdballows debugging of enclaves
-
- The library is divided into 3 functional components (1):
- sgx-ssl is a port of OpenSSL to be executed inside SGX enclaves, which provide cryptographic primitives to enclaves, e.g., for key signing.
- DCAP (Data Center Attestation Primitives) provides two main libraries which are important in remote attestation.
- Quote generation allows an enclave to generate a quote, which includes the measurement (hash) of its initial state.
- Quote verification enable a remove verifier to verify a generated quote.
Interactions
Below are my attempts at providing an overview of how the software components interact with each other. Generally, the development stages of an enclave application can be classified into build time and deployment time.
The diagrams contain all the components (and subcomponents) that were mentioned above. Note that this is heavily simplified, and may be also incorrect, as it reflect my current understanding.
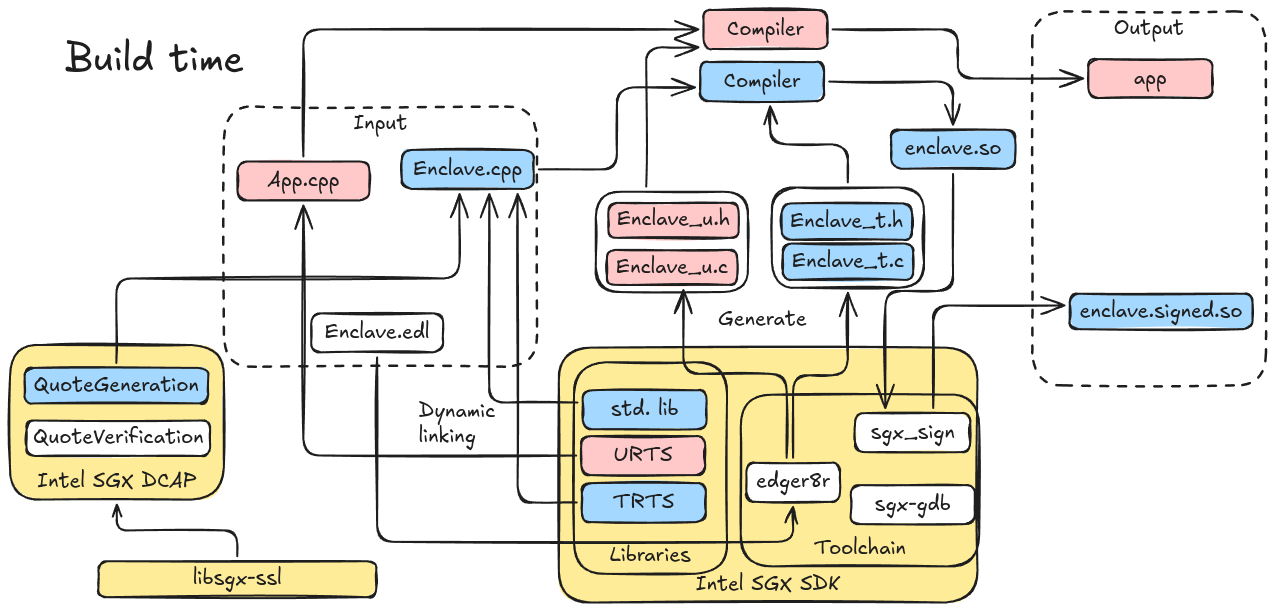
Build time
The goal of building phase is to compile the source files of the enclave and the untrusted application, and an specification for the interface between them written in Enclave Definition Language (EDL). The output are (1) a signed enclave ELF and (2) the untrusted application, which is a normal ELF file.
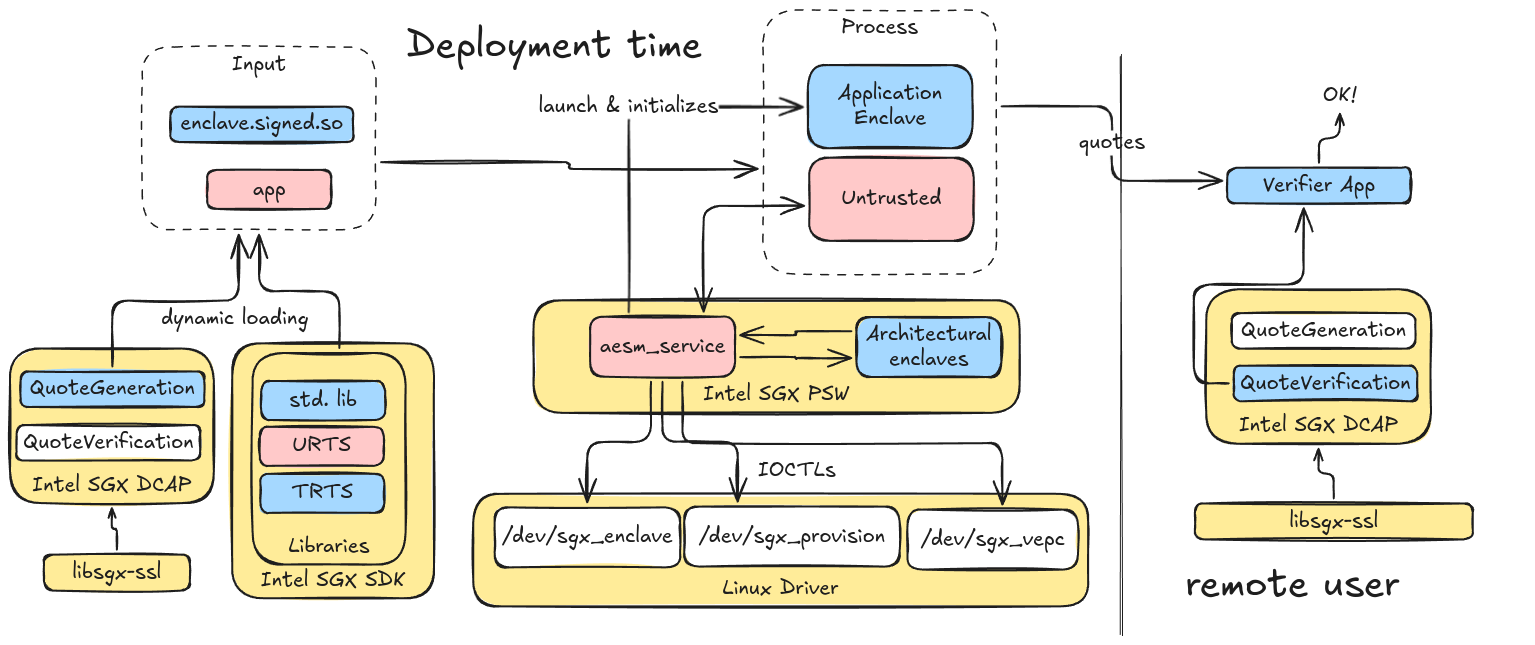
Deployment time
To deploy an enclave, the untrusted part of the enclave application communicate with aesm_service to create and initialize the enclave.
Distribution
Intel provides a prebuilt version for most components, so the users don’t have to rebuild them from scratch. They can be accessed at https://download.01.org/intel-sgx/latest/linux-latest/
The driver for SGX is built into most modern Linux distribution (since Linux 5.11 3), so manually installing them is not encouraged.